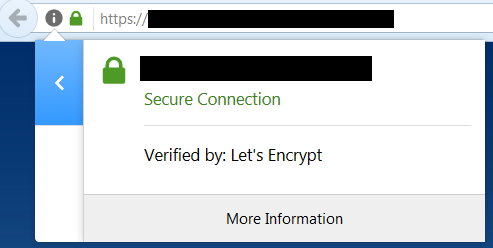
To achieve a more successful phishing campaign and to protect client credentials in transit, adding an SSL certificate to your phishing pages can a great addition.
This guide assumes that you already have GoPhish set up and a phishing domain registered. For detailed instructions on how to set up GoPhish, review their documentation.
To get an SSL certificate for your domain with LetsEncypt, it is as simple as running:
wget https://dl.eff.org/certbot-auto
chmod a+x certbot-auto
./certbot-auto certonly -d {your domain} --manual --preferred-challenges dns
This will pull down CertBot and automatically install all required dependencies. It will also use DNS validation to prove domain ownership, I’ve found this to be the easiest option. Follow the on-screen prompts until “Please deploy a DNS TXT record under the name”.
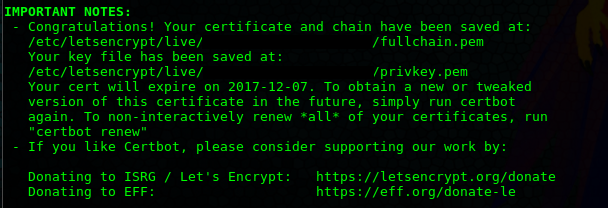
I typically use GoDaddy for domain registration. If you are using GoDaddy, you can go to https://dcc.godaddy.com/manage/[DOMAIN]/dns to mange the DNS settings for your domain. Just add a TXT record with Host field populated with the name provided from CertBot, and the Value field populated with the random value provided by CertBot. Wait a little bit for the DNS records to propagate, and then press enter to continue. You should see a message like this:
 The next step is to log in to your GoPhish server if you are not already on there. Go to the GoPhish directory (likely under /opt/gophish) and copy the files generated by LetsEncrypt. Go ahead and copy /etc/letsencrypt/live/[DOMIAN]/privkey.pem into a file like [DOMAIN].key and /etc/letsencrypt/live/[DOMAIN]/fullchain.pem into a file like [DOMAIN].crt. The next thing to do is change the config.json file. You want to modify the “phish _server” parameter to look similar to this:
The next step is to log in to your GoPhish server if you are not already on there. Go to the GoPhish directory (likely under /opt/gophish) and copy the files generated by LetsEncrypt. Go ahead and copy /etc/letsencrypt/live/[DOMIAN]/privkey.pem into a file like [DOMAIN].key and /etc/letsencrypt/live/[DOMAIN]/fullchain.pem into a file like [DOMAIN].crt. The next thing to do is change the config.json file. You want to modify the “phish _server” parameter to look similar to this:
"phish_server" : {
"listen_url" : "0.0.0.0:443",
"use_tls" : true,
"cert_path" : "[DOMAIN].crt",
"key_path": "[DOMAIN].key"
},
It may be necessary to kill the running GoPhish process. I use ps aux to find the PID and then use the kill command to end the process.
Restart GoPhish with:
./start_gophish.sh
Validate that port 443 is open and listening:
/sbin/iptables --list netstat -nao
You should see a message like this in the console when running the script:
Starting phishing server at https://0.0.0.0:443
When creating you campaigns, all you need to do from this point is make sure the URL parameter when starting a new campaign is populated with the HTTPS protocol prefix as opposed to HTTP.
If all goes well, you phishing site should give you a green lock.